Server Name Indication (SNI) in Win 2012 Server / IIS 8.0
What is SNI?
On Windows Server 2012, IIS supports
Server Name Indication (SNI), which is a TLS extension to include a virtual
domain as a part of SSL negotiation. What this effectively means is that the
virtual domain name, or a hostname, can now be used to identify the network end
point
What is the Problem with Win 2008 R2 Or IIS 7.0 / 7.5?
It is not possible When I want multiple
https sites to be hosted using 443 port on Win 2008 R2 (IIS 7.0/7.5) server
which has single IP. While trying to host so, IIS won’t allow doing so and if
we force then the SSL cert will be replaced on another site already on 443
port. So the only solution is to get additional IPs and bind the same to https
sites on 443 port.
Let’s
see this in action…
Below
is an IIS Site running on 443 port, just think of as a typical SharePoint’s web
application.
Here
we have single IP and https binded to 443.
Now
if I want to create another site with same IP and https on 443, not possible.
We will get into below mess up.
Note
– even though you provide different host header with 443 and same IP combination,
it won’t work!
On
Windows Server 2012, IIS supports Server Name Indication (SNI), which is a TLS
extension to include a virtual domain as a part of SSL negotiation. What this
effectively means is that the virtual domain name, or a hostname, can now be
used to identify the network end point. In addition, a highly scalable
WebHosting store has been created to complement SNI. The result is that the
secure site density is much higher on Windows Server 2012 and it is achieved
with just one IP address.
It
should be noted that in order for this feature to be used, your client browsers
have to support SNI. Most modern browsers support SNI; however, Internet
Explorer (of any version) on Windows XP does not support SNI.
Let’s
see the same in action.
Here
we have single IP and https binded to 443.
Now
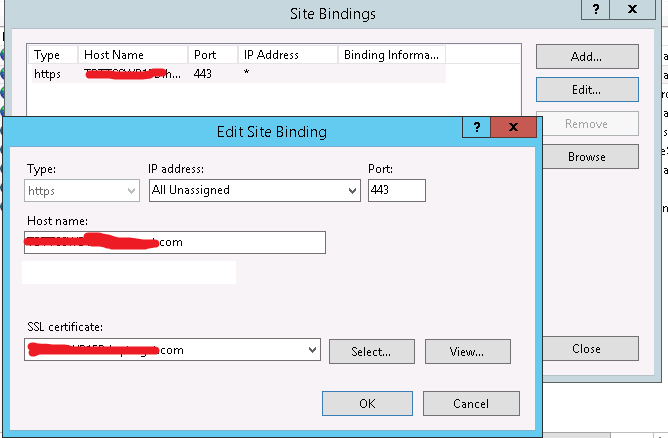
if I want to create another site with same IP and https on 443, it is possible
with the use of SNI a as shown below. Ensure you check “Required Name
Indication”.
The
same way you can create any number of https sites through SharePoint with the
combination of “same IP:443 port”.
SCENARIOS
Try
deploying the following scenarios:
·
SNI is designed to scale for a
multi-tenanted environment. Try configuring thousands of secure sites using
SNI.
·
Unlike previous versions of
Windows Server, the certificates on Windows Server 2012 are loaded in memory
on-demand. After configuring thousands of secure sites using SNI, send a GET
request to one of the secure sites and observe the memory usage. It is
negligible. On previous versions of Windows Server, if hundreds of secure sites
are configured, sending just one GET request would cause the Windows Server to
load all certificates,
resulting in a high memory usage, and further limits the scalability.
·
Configure Windows Server 2012 with
both SNI and traditional secure sites. They are designed to co-exist.
Reference


Comments
Post a Comment